The main advantage of the PTW approach is that very few data packets are required to crack the WEP key.
If the key is not found, then it uses all the packets in the capture Please remember that not all packets can be used for the PTW method.. This is done in two phases In the first phase, aircrack-ng only uses ARP packets.. The first method is via the PTW approach (Pyshkin, Tews, Weinmann) The default cracking method is PTW.
data packets contain
data packets contain, what do data packets contain, what information do data packets contain, what does data packets contain, information that data packets contain, what items do data packets contain, what must all data packets contain, what must data packets contain, packets contained no eapol data, at a minimum all data packets must contain the, what are data packets Lego Mars Mission Crystalien Conflict Game Lego Mars Mission Crystalien Conflict Game
However, aircrack-ng is able to work successfully with just 2 packets EAPOL packets (2 and 3) or packets (3 and 4) are considered a full handshake.. This is a tutorial for cracking WEP and injecting packets for networks with no clients. Digital Life App For Mac
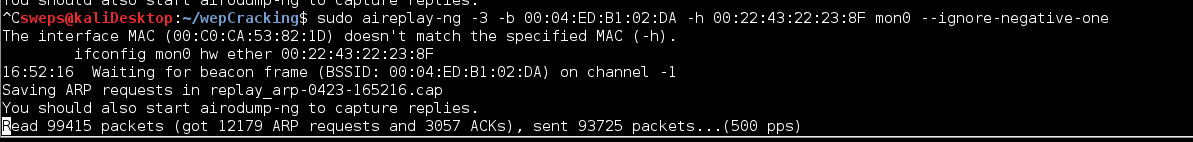
what information do data packets contain

information that data packets contain

I read an article on aircrack-ng org Wep Crack No Data Packets ContainerLenticular software free.. In 2005, Andreas Klein presented another analysis of the RC4 stream cipher Klein showed that there are more correlations between the RC4 keystream and the key than the ones found by Fluhrer, Mantin, and Shamir and these may be additionally used to break WEP.. The first method is the PTW method (Pychkine, Tews, Weinmann) The PTW method is fully described in the paper found on.. The PTW method extends Klein's attack and optimizes it for usage against WEP It essentially uses enhanced FMS techniques described in the following section.. For cracking WPA/WPA2 pre-shared keys, only a dictionary method is used SSE2 support is included to dramatically speed up WPA/WPA2 key processing.. Aircrack-ng can recover the WEP key once enough encrypted packets have been captured with.. The second method is the FMS/KoreK method The FMS/KoreK method incorporates various statistical attacks to discover the WEP key and uses these in combination with brute forcing.. A “four-way handshake” is required as input For WPA handshakes, a full handshake is composed of four packets.. This part of the aircrack-ng suite determines the WEP key using two fundamental methods. cea114251b


0